- Cloud-Native Products
- Digital-Native Products
- Infrastructure Products
- Services
- By Industry
- Featured Solutions
- Cooperative Partner


Based on sensitive data marked in the data classification hierarchy list (critical/core level or level 3/4), data’s static desensitization is typically applied to process batch of data under enterprises’ development test environment following certain rules and algorithms, such as preserving format encryption, replacement, deletion, encryption, etc., make the original data unreadable and unidentifiable, and ensure data security. Meanwhile, the desensitized data is featured by uniqueness, emulation, relevance, etc., which is same to the original data, meeting the constraint verification of database and rule verification of business data, and supporting desensitization competence of more than 70 isomorphic and heterogeneous data sources.
- User pain point
- Program feature
- Application scenario
• Huge investment in “application system transformation”;
• Line business application system cannot realize strong association between application user permission and sensitive data masking (data);
• Data breaches cannot be traced accurately.
When sensitive data in production environment is delivered to development, testing, or outbound environment, data’s static desensitization is widely adopted and large batches of data are transformed at one time according to desensitization rules. While reducing the sensitivity of data, it can retain the intrinsic correlation of data possessed by the original data set to the greatest extent and other mine other values.
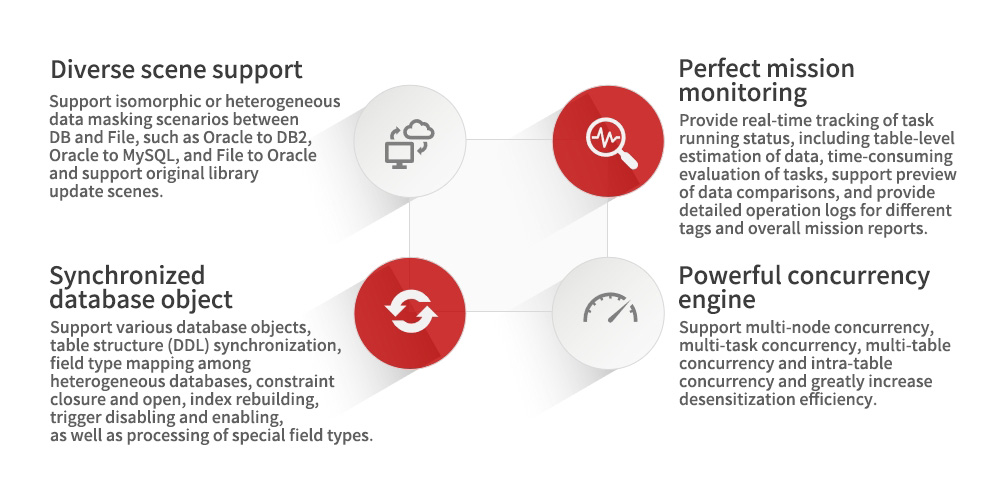
Suitable for desensitizing data extracted from production environment and distributing to testing, development, training, data analysis and other scenarios.
© 2016-2024 Digital China Group Co., Ltd., All rights reserved. Jing ICP Bei No. 05051615-1  Jing Gong Wang An Bei No. 11010802037792
Jing Gong Wang An Bei No. 11010802037792