- Cloud-Native Products
- Digital-Native Products
- Infrastructure Products
- Services
- By Industry
- Featured Solutions
- Cooperative Partner


- User pain point
- Program feature
- Application scenario
• Huge investment in “application system transformation”;
• Failed to construct a strong correlation between application user permission and sensitive data masking in current business application system;
• Hard to trace data leakages precisely
• Based on sensitive data marked in the data classification hierarchy list (critical/core level or level 3/4), parse database access requests by proxy in real time;
• Desensitize data return results according to certain rules and algorithms, make the original data unreadable and unrecognizable, and ensure data security.
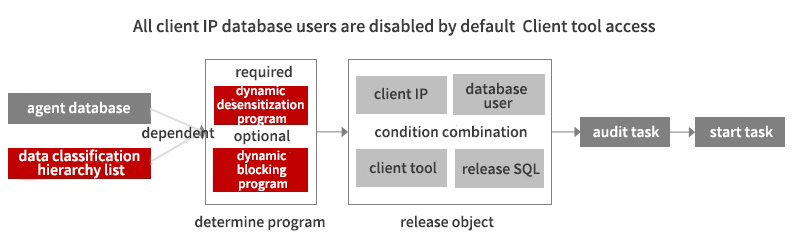
Suitable for “real-time” desensitization of queries and call results for sensitive data and other scenarios without departing from the production environment.

© 2016-2024 Digital China Group Co., Ltd., All rights reserved. Jing ICP Bei No. 05051615-1  Jing Gong Wang An Bei No. 11010802037792
Jing Gong Wang An Bei No. 11010802037792