- Cloud-Native Products
- Digital-Native Products
- Infrastructure Products
- Services
Data Intelligence
- By Industry
- Featured Solutions
- Cooperative Partner


Data Security Sharing
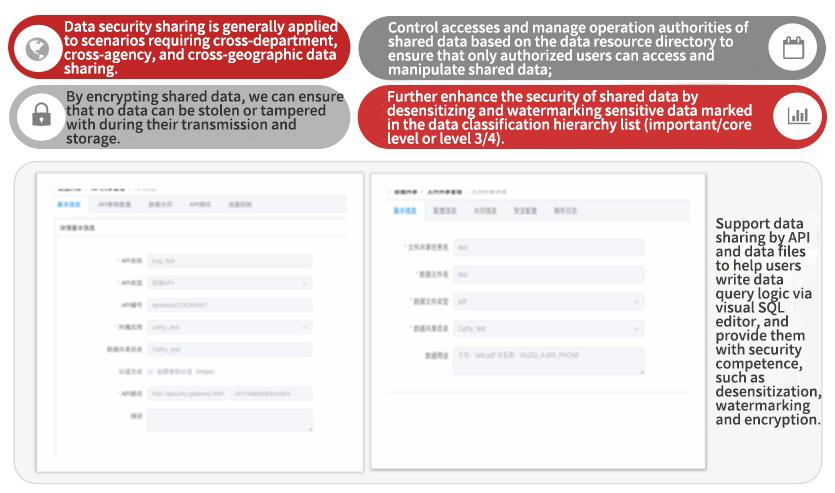
By encrypting shared data, we can ensure that no data can be stolen or tampered with during their transmission and storage
Feature of Data Security Sharing
- user pain point
- Program feature
- Application scenario
user pain point
• Lack integrity during data security operations
• Difficult to map data assets
• Incomplete data security protection system
Program feature
• Control accesses and manage operation authorities of shared data based on the data resource directory to ensure that only authorized users can access and manipulate shared data;
• Further enhance the security of shared data by desensitizing and watermarking sensitive data marked in the data classification hierarchy list (important/core level or level 3/4).
Application scenario
Data security sharing is generally applied to scenarios requiring cross-department, cross-agency, and cross-geographic data sharing.
Please fill in your requirements:
Stock Code:000034.SZ
Related Websites
Follow us on Digital China
© 2016-2024 Digital China Group Co., Ltd., All rights reserved. Jing ICP Bei No. 05051615-1  Jing Gong Wang An Bei No. 11010802037792
Jing Gong Wang An Bei No. 11010802037792