- Cloud-Native Products
- Digital-Native Products
- Infrastructure Products
- Services
- By Industry
- Featured Solutions
- Cooperative Partner
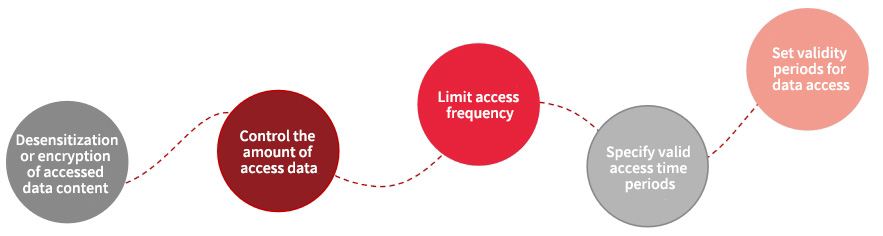
Multi-dimensional data access behavior control. By establishing roles and authority systems, we authorize users’ data access behaviors, configure their security access policies as per their authority and security level of access data, support desensitization and encryption of accessed sensitive data, control the amount of access data, limit access frequency and specify valid access time periods, and directly block access data in non-specified time periods. In addition, we can set validity periods for data access, during which only specified data can be accessed.
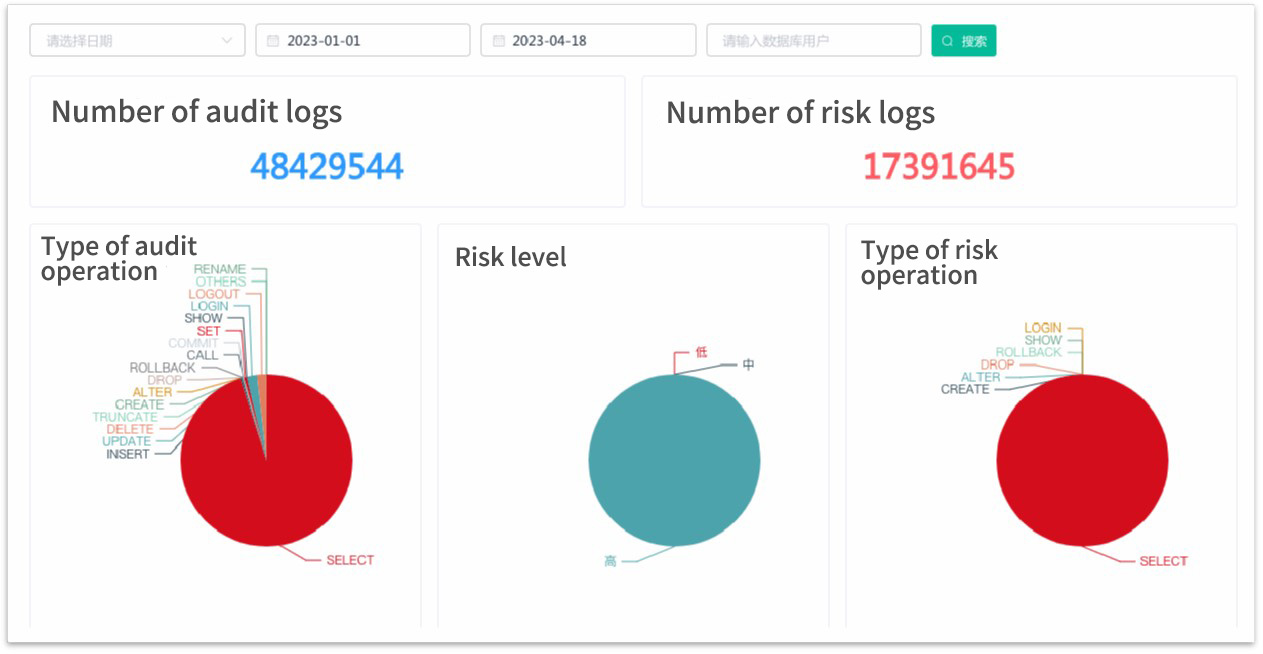
We can record login, logout, DDL, DCL, DML and other operation behaviors of users in database At length and provide strong evidence for behavior tracing in view of any risk.
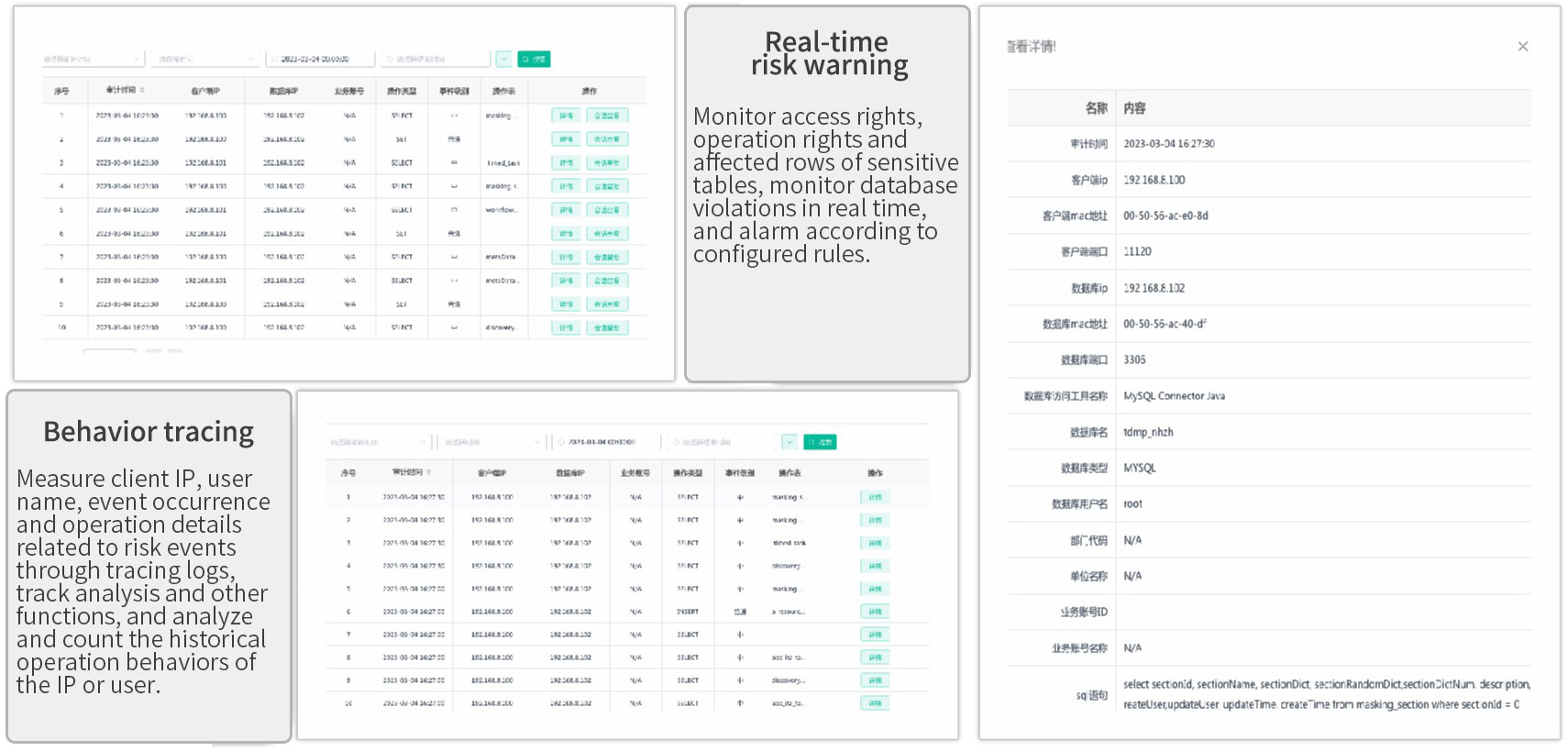
Trace all the previous relevant operation records from a system, a component, or an event, and finally figure out the whole accident; trigger the relevant alarm notification in the light of an event or an abnormal behavior.
© 2016-2024 Digital China Group Co., Ltd., All rights reserved. Jing ICP Bei No. 05051615-1  Jing Gong Wang An Bei No. 11010802037792
Jing Gong Wang An Bei No. 11010802037792

