Full-scenario Security Consulting Services
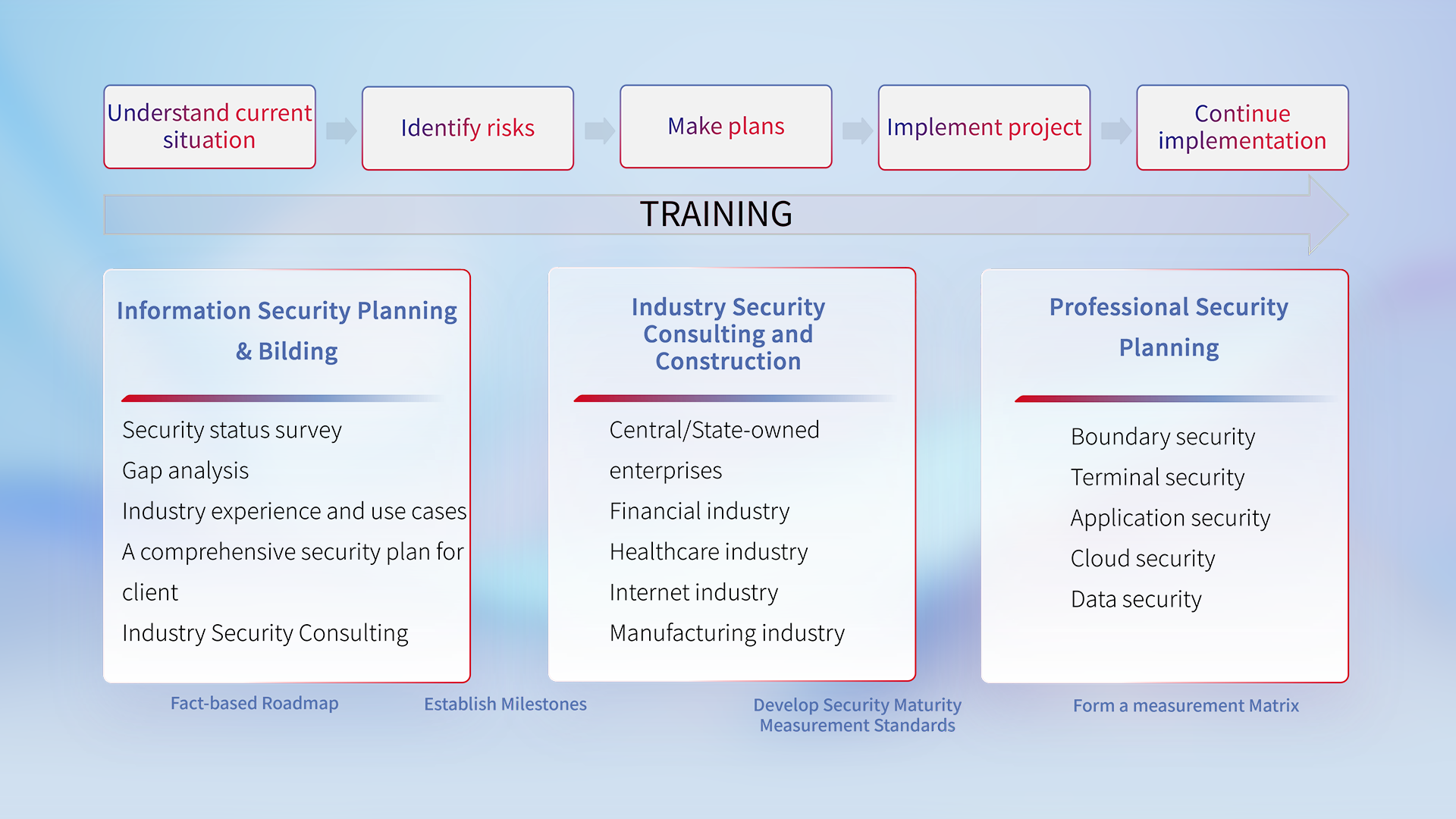
Based on the customer's information security status survey and gap analysis results, combined with industry advanced experience and best practices, we formulate the customer's information security control system summary architecture. Ultimately, form a complete panorama of the customer's information security planning and construction.
Level Protection Consulting Services
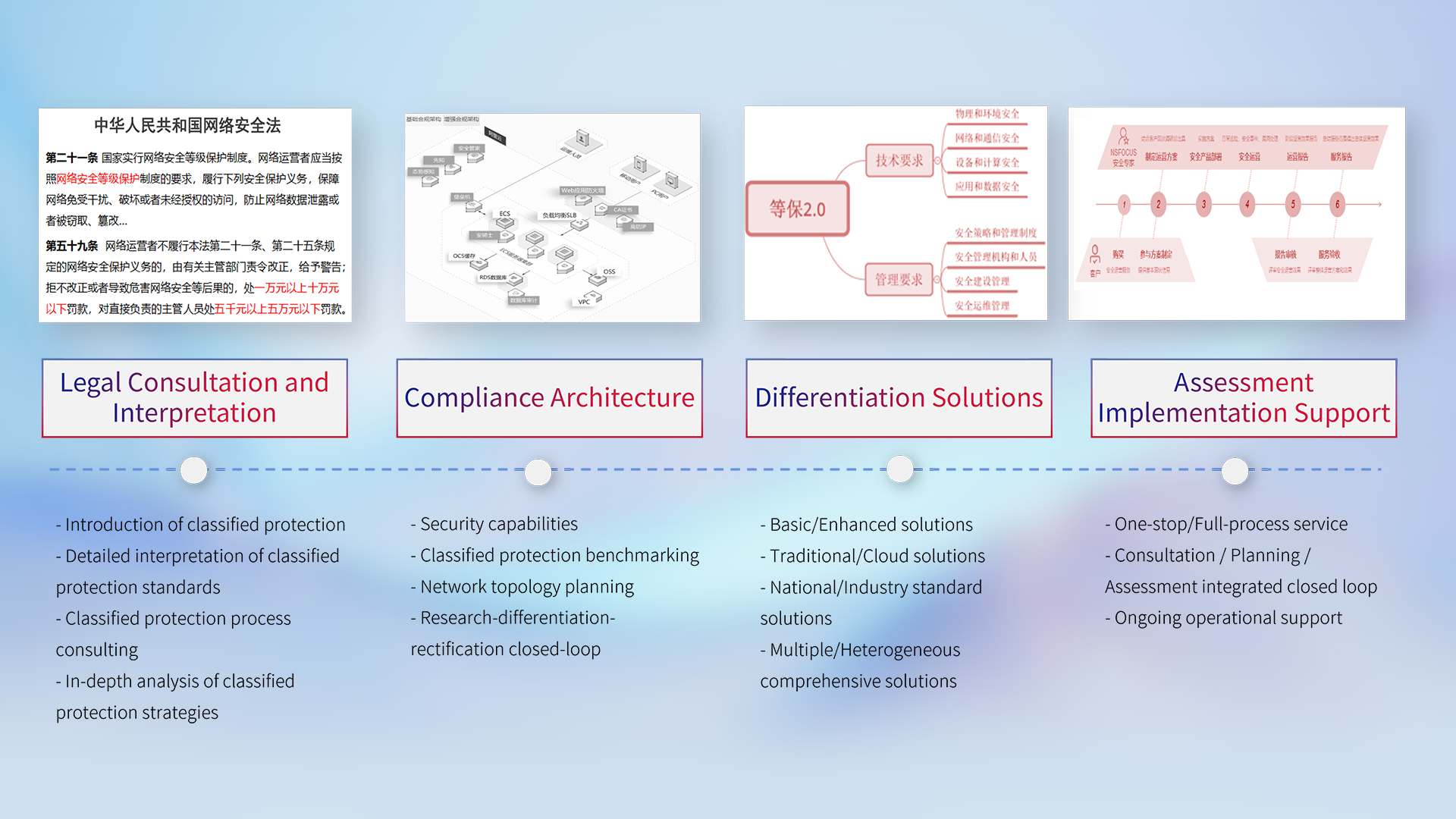
Level protection is China's basic policy on information security. Through professional legal consulting interpretation, compliance architecture embodiment, differentiated solutions, and test implementation support services, we create a level protection compliance system tailored to the customer.
Integrated Delivery Services
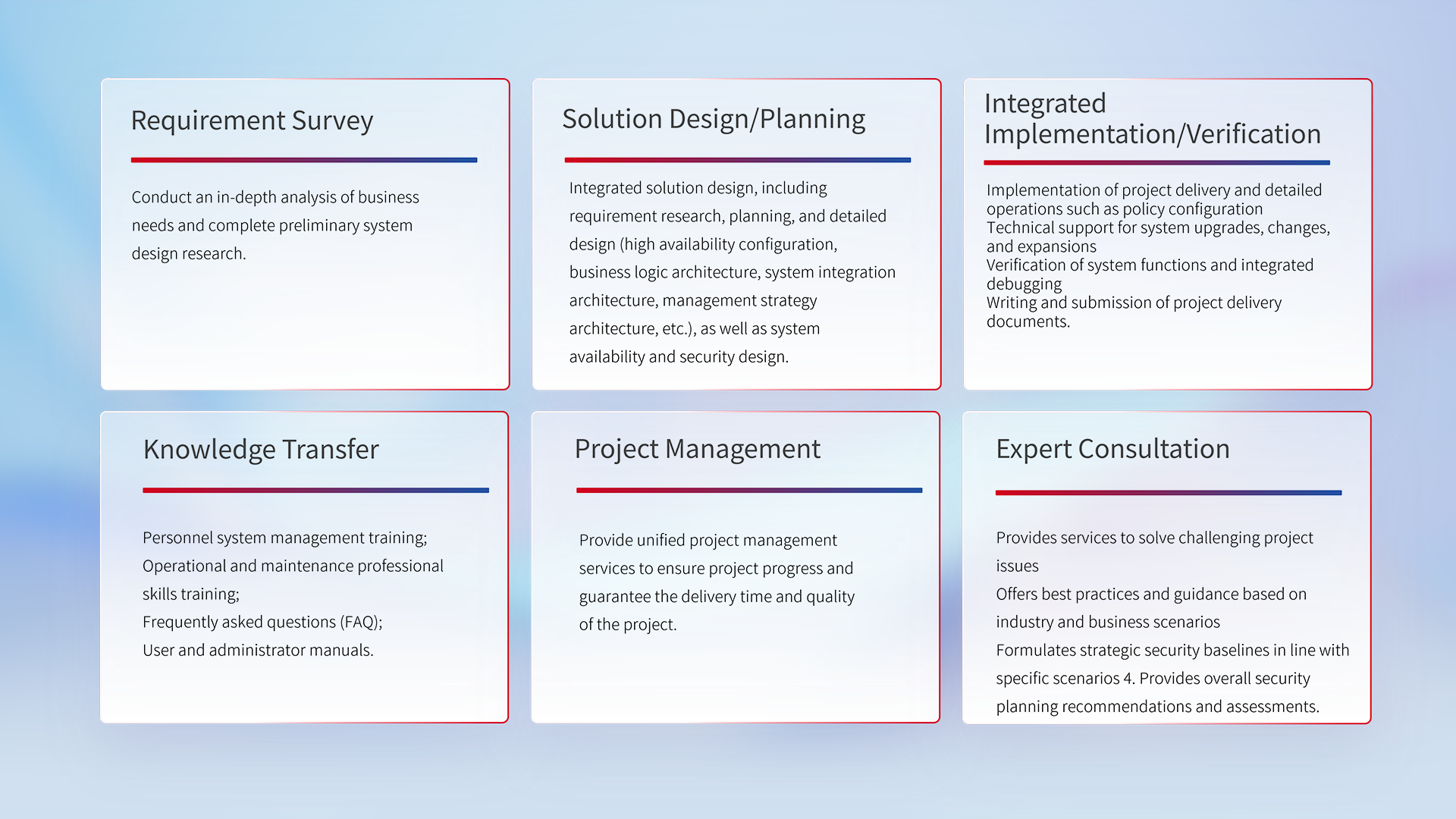
According to the customer's industry characteristics, the macro security strategy and needs are realized through professional delivery services, providing customers with standardized and integrated delivery services.
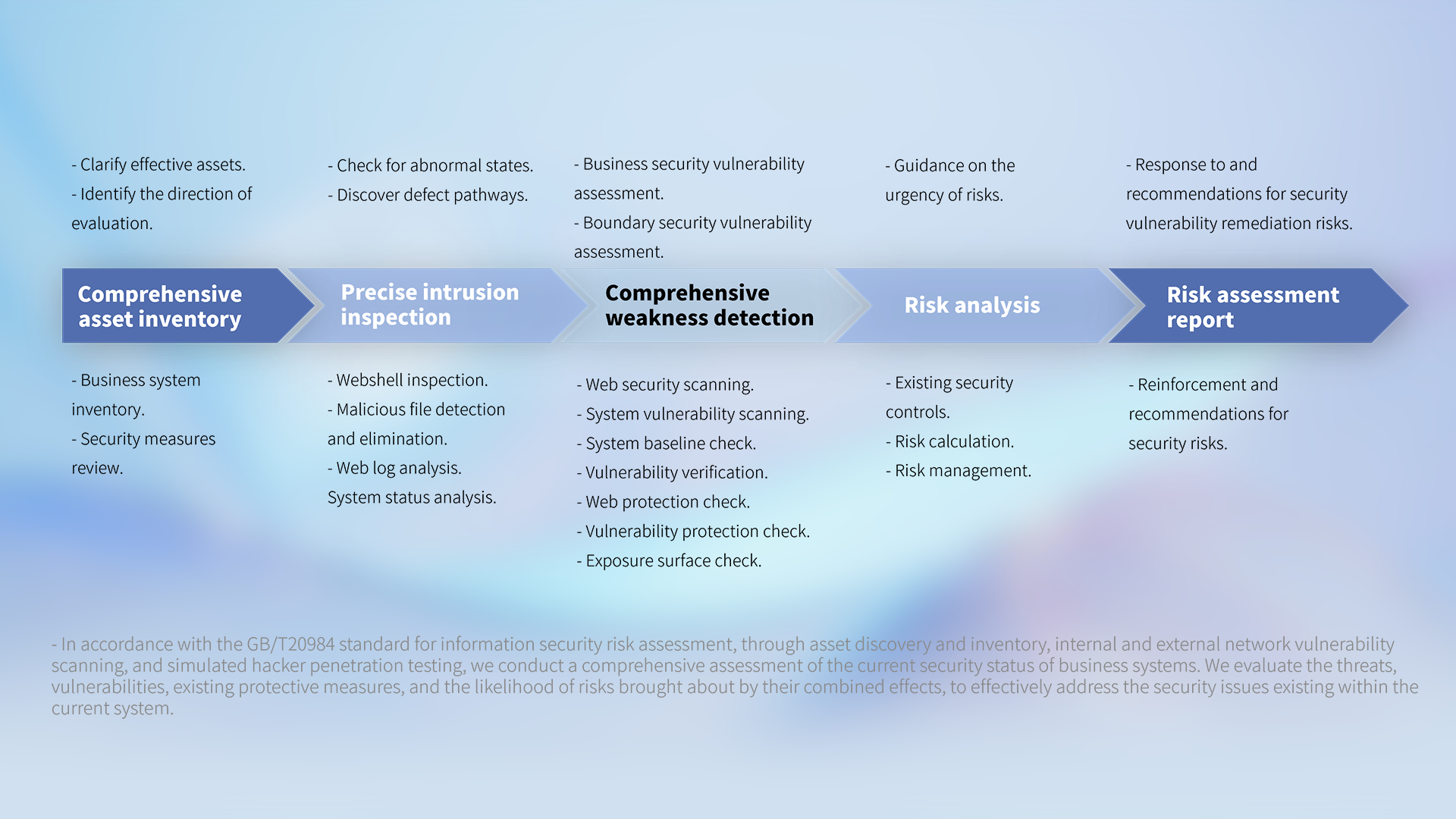
Assessment and Validation Services
Help customers quickly discover, combat, and deal with threats, providing professional analysis perspectives and reports.
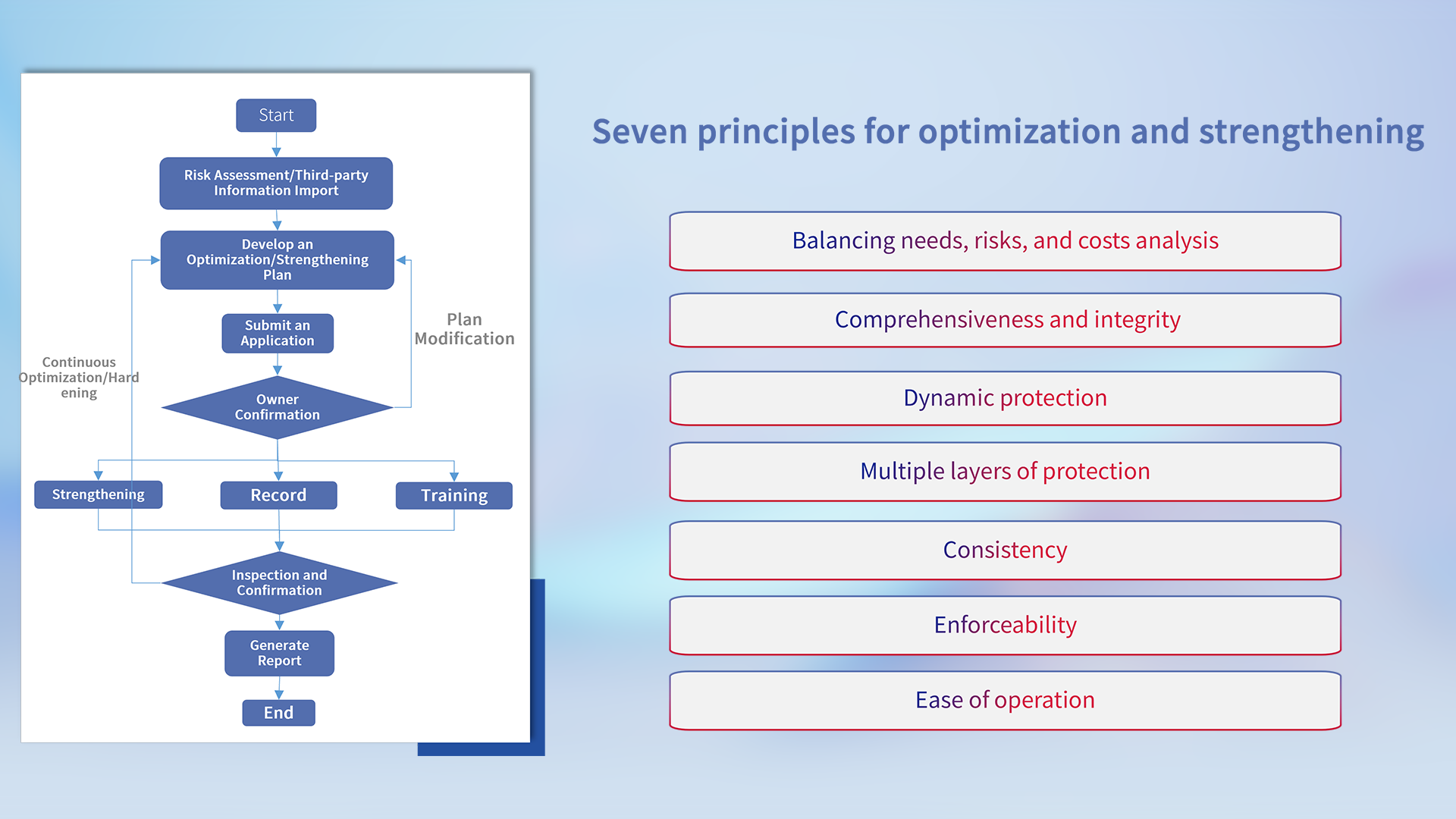
Optimization and Reinforcement Services
Make full use of existing assets to block and rectify problems found in the assessment, prevent the use of vulnerabilities, enhance overall network security, and provide customers with high-standard optimization and reinforcement services.
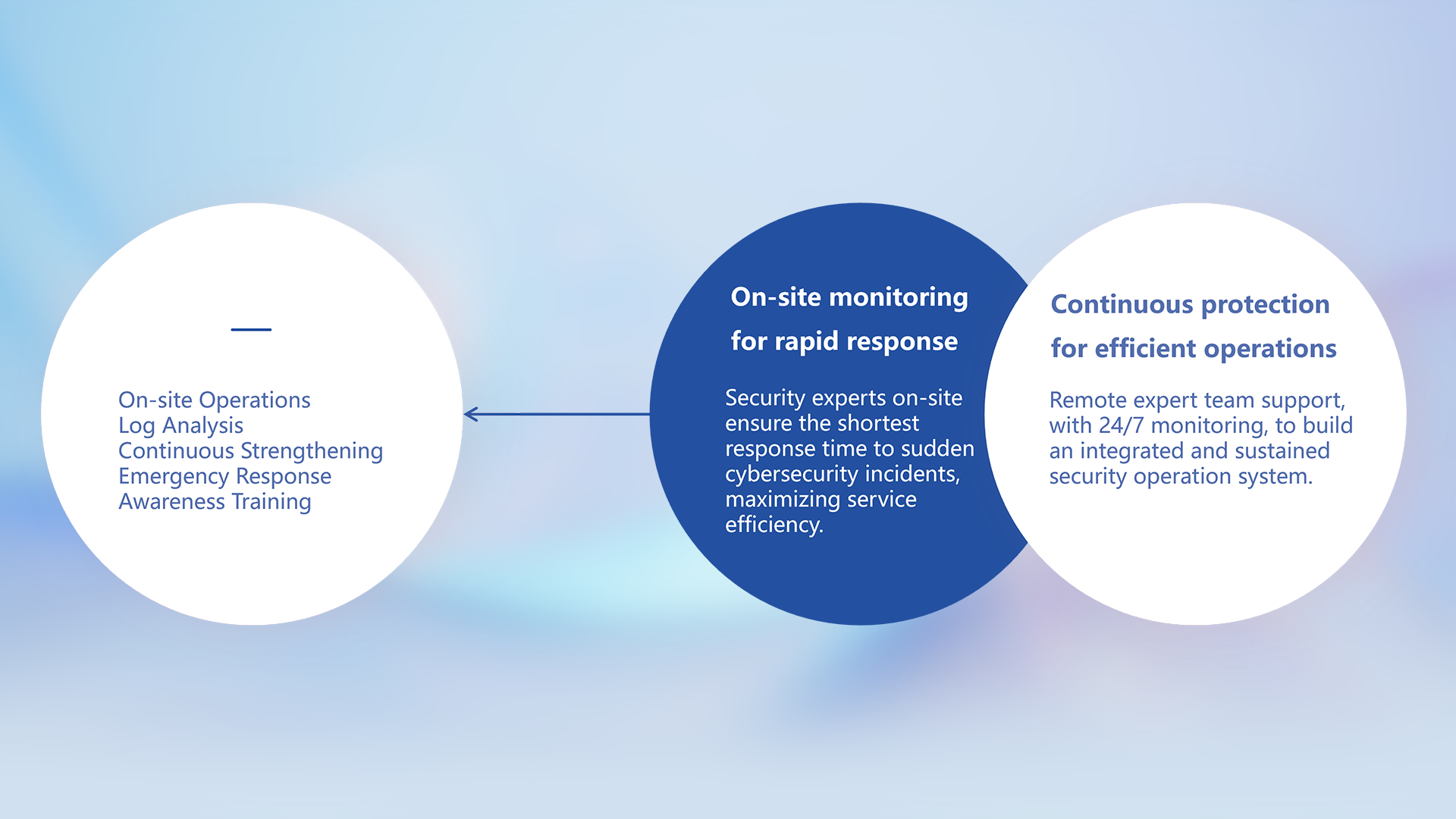
Operation and Maintenance Services
Continuously monitor security events 24/7, maintain the effectiveness of security policies, reduce asset vulnerability risks, accurately intercept hacker attacks, reduce the chances of being exploited by hackers, and curb them at the first moment to reduce losses.
 Smart Vision
Smart Vision Shenzhou Kuntai & Smart Vision Integrated GenAI Suite
Shenzhou Kuntai & Smart Vision Integrated GenAI Suite Data Asset Accounting
Data Asset Accounting Data Security Control Platform
Data Security Control Platform Shenzhou Yanyun Integrated Solutions
Shenzhou Yanyun Integrated Solutions Cloud Management Services
Cloud Management Services AI Computing Power Servers
AI Computing Power Servers Storage Products
Storage Products Low-Altitude Solution
Low-Altitude Solution RaaS Operation Service Solution
RaaS Operation Service Solution