Network Architecture Optimization and Asset Management:
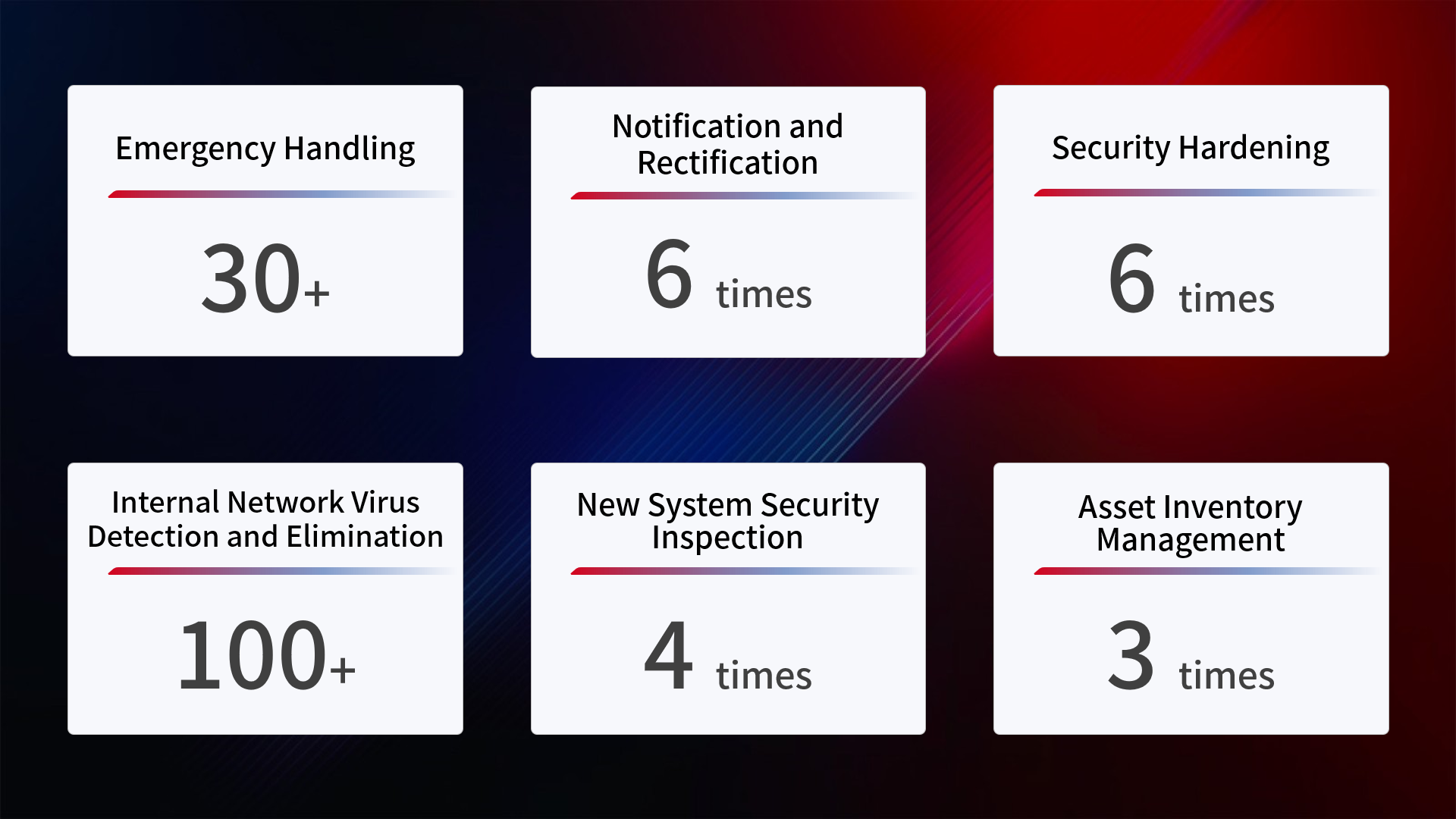
Assist the hospital in optimizing the complex network architecture to improve manageability and efficiency.
Sort out network assets, establish and improve network management systems to ensure clarity and control over network assets.
Enhancement of Security Level and Incident Response:
Deploy experienced security engineers to enhance the overall level of the hospital's cybersecurity protection.
Establish and improve the process for handling sudden cybersecurity incidents to increase response speed and handling capabilities.
Regulatory Reporting and Rectification:
Assist the hospital in promptly dealing with reports from higher regulatory authorities to ensure timely completion of rectification requirements. Through rectification, reduce the number of times the hospital is reported, minimizing potential compliance risks.
Cybersecurity Reinforcement and Risk Management:
Use technical reinforcement methods, such as strengthening zone isolation, to reduce the scope of potential internal network attacks.
Optimize existing network security management systems to achieve systematic management, reduce exposure to network threats, decrease the likelihood of being hacked, and implement effective responses to sudden security incidents to minimize potential losses.
 Smart Vision
Smart Vision Shenzhou Kuntai & Smart Vision Integrated GenAI Suite
Shenzhou Kuntai & Smart Vision Integrated GenAI Suite Data Asset Accounting
Data Asset Accounting Data Security Control Platform
Data Security Control Platform Shenzhou Yanyun Integrated Solutions
Shenzhou Yanyun Integrated Solutions Cloud Management Services
Cloud Management Services AI Computing Power Servers
AI Computing Power Servers Storage Products
Storage Products Low-Altitude Solution
Low-Altitude Solution RaaS Operation Service Solution
RaaS Operation Service Solution